Proactively address risk—with the only CSPM
purpose-built for healthcare.
Generic cloud security posture management (CSPM) solutions can protect, well, generic data.
The ClearDATA CyberHealth™ Platform is made exclusively to protect PHI and other sensitive healthcare data in the cloud.
Secure healthcare data.
Our 300+ safeguards align with critical healthcare regulations including HIPAA, HITRUST, NIST, GDPR, and more.
Streamline compliance.
Transform regulatory challenges into manageable tasks, translating intricate healthcare regulations into actionable technical controls.
Prioritize & remediate threats.
Get a comprehensive view of cloud security posture with intuitive dashboards designed to anticipate, mitigate, and remediate vulnerabilities before they become liabilities.
Simplify the complexities of cloud security.
With unrivaled visibility and control, you can focus on what matters: Improving the state of healthcare.
Know and improve your cloud compliance, security, and privacy posture, and stay aligned with HIPAA, HITRUST, GDPR, SOC 2, ISO27001 and more.
Want customizable options?
Our cloud security and compliance plans and packages are tailor-made for healthcare.
Features for Cloud Security Posture Management
A suite of powerful features to protect your cloud environments and enhance your operational efficiency.
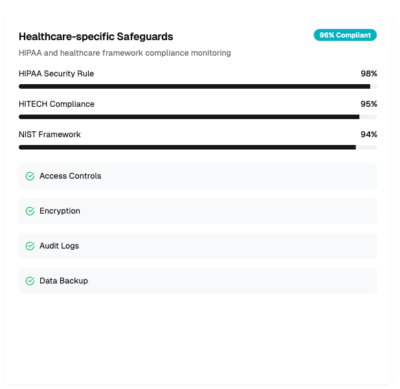
Healthcare-specific safeguards
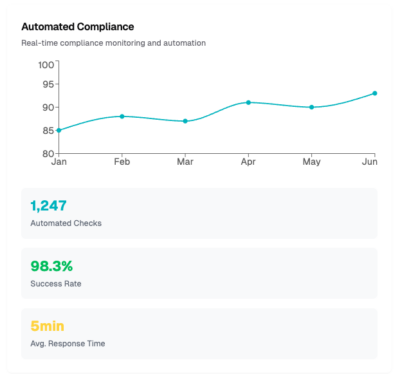
Automated compliance
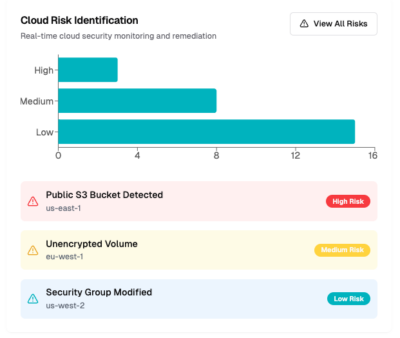
Cloud risk identification and remediation
Compliance risk scores and remediation dashboards
PHI leak discovery
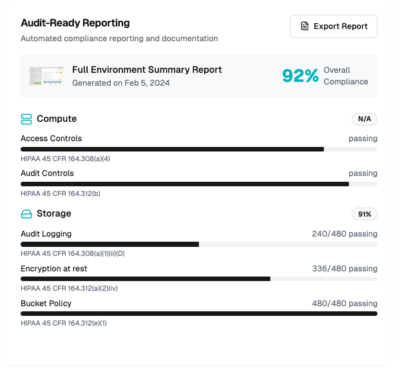
Audit-ready reporting
Safeguards to Futureproof Against Threats
Backed by 300+ healthcare-specific safeguards, including HIPAA, HITRUST, HITECH, NIST, GDPR, and more, the CyberHealth™ Platform provides continuous security and compliance enforcement tailored for the complexities of healthcare cloud environments.
With real-time risk monitoring, automated remediation, and proactive threat defense, our platform ensures your cloud infrastructure stays resilient against evolving cyber threats, so you avoid costly breaches, and future-proof your cloud architecture.
Cloud Partners
Credentialed. Celebrated. Certified.