Healthcare organizations dealing with PHI are obliged to monitor their compliance posture and remediate the occurrence of any violation of compliance standards and regulations. ClearDATA’s Automated Safeguards automate the technical controls that must be configured within different cloud services to keep your organization’s environment compliant. You can learn more about Automated Safeguards here.
However, many healthcare organizations still have the responsibility to investigate a non-compliant action when it occurs and generate a documented plan to keep it from happening again. While our Automated Safeguards keep you secure and compliant within your Google Cloud environment by enforcing controls such as logging or encryption, it’s best to try to follow good compliance practice when you can. I’m excited to share that we now provide an Automated Safeguard Data Feed for Google services, which gives you a history of every action an Automated Safeguard enforced or remediated. This can help many teams understand how they are violating the specific compliance policy. Proactive review of these feeds can help you understand how to adjust and improve your team’s best practice. Additionally, it provides documented evidence that proves your efforts to secure PHI should you need it for future audit reports.
This article will address how to monitor and be alerted of any remediation action taken by ClearDATA’s Automated Safeguards.
Automated Safeguard Data Feed Via Stackdriver Logging
ClearDATA’s Automated Safeguards insert a convenient log message into customer projects if remediation has occurred. This can provide a trigger point for clients to build notification events in log monitoring tools they already have in place and provide a starting point for preventing that occurrence from happening again. Let’s take a look at the format of the log event created when a storage bucket is created without versioning enabled:
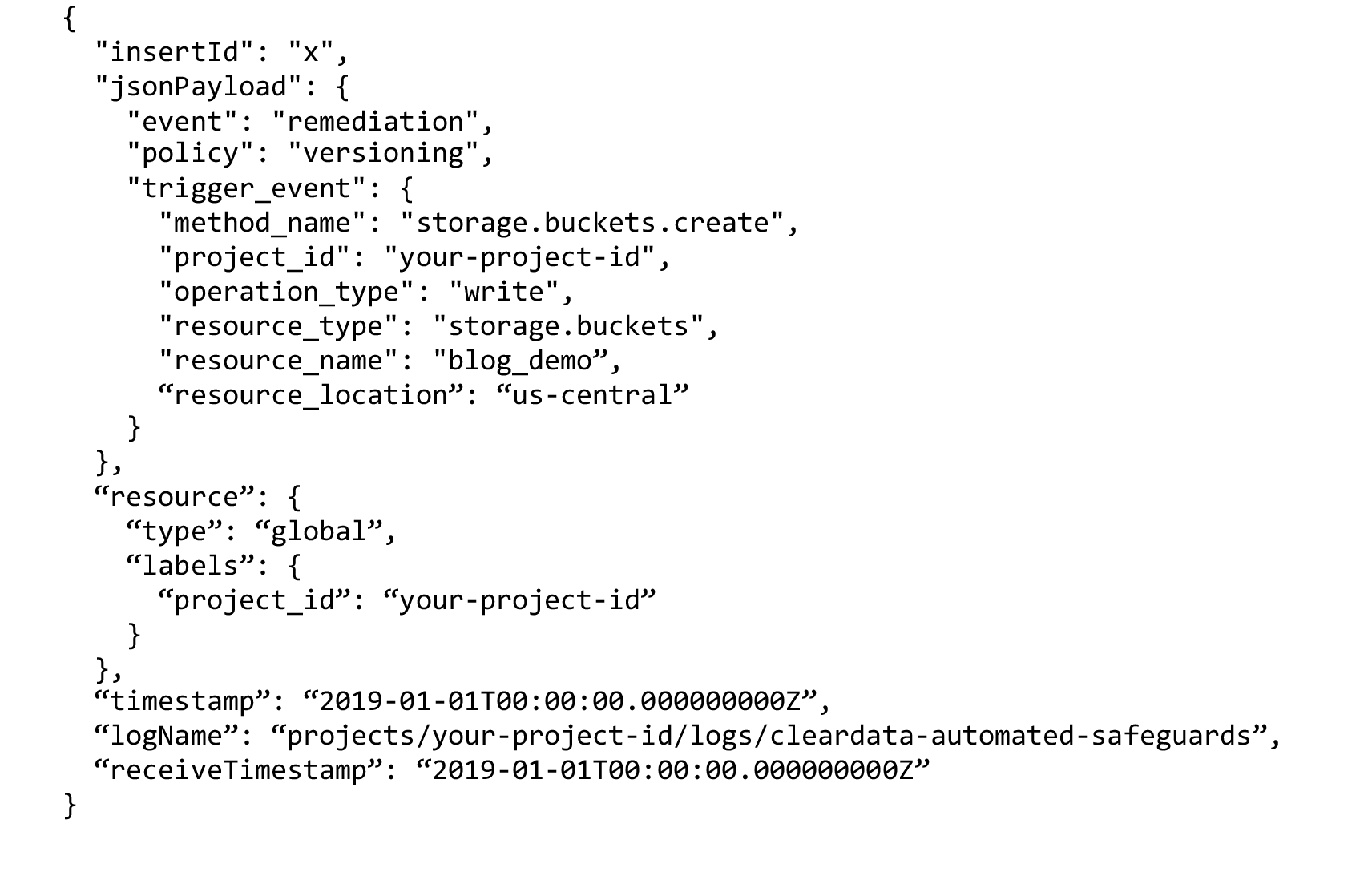
As you can see above, the resource type “storage.buckets,” a Google Cloud Storage Bucket, was created, and the Automated Safeguard was triggered by the method “storage.buckets.create.” A logging event is only created when remediation occurs, and in this case, the policy for “versioning” was enforced. Clients can view all of these log events in Stackdriver within the project they occur in, unless all of the customer logs are synced to a centralized logging project. In that case, it would be easy to locate Automated Safeguard remediation events across all of the projects in a customer organization. Here’s an example of an advanced filter used to find Automated Safeguard remediation events in Stackdriver’s user interface:
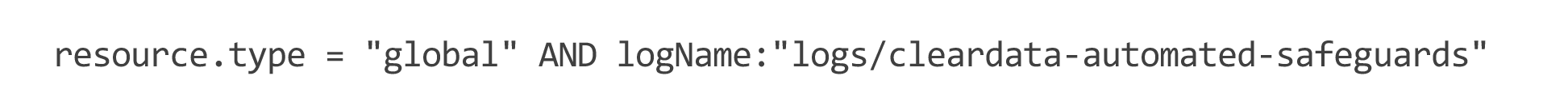
That Stackdriver query will return all Automated Safeguard remediation actions performed by ClearDATA for projects onboarded with ClearDATA. To run the query, go to https://console.cloud.google.com/logs/, select the ▼ in the search box, and select “Convert to advanced filter.”
Alerting Based on the Automated Safeguard Data Feed
Alerting can be achieved by exporting Stackdriver logs, called log syncs, into another tool that can alert based on the detection of an Automated Safeguard remediation event. Logging sinks can be configured per-project, folder, or organization, and can deliver the data to BigQuery, PubSub, or Cloud Storage. For example, this will create an organization-level sink that exports all remediation logs to Pub/Sub using a gcloud command:

That Pub/Sub topic can then be subscribed to by a variety of different tools, the most popular being Splunk. Take a look at Splunk’s documentation on how to subscribe to a Pub/Sub Topic: https://docs.splunk.com/Documentation/AddOns/released/GoogleCloud/Configureinputsv1modular
What to do After a Remediation Event Occurs
ClearDATA’s Automated Safeguards provide a solution to HIPAA 45 CFR §64.530 (c)(1) that dictates “Standard: Safeguards. A covered entity must have in place appropriate administrative, technical, and physical safeguards to protect the privacy of protected health information.” As a result of remediation actions taken by ClearDATA on behalf of clients, it may indicate a need for training, as required by HIPAA 45 CFR §164.530(b)(1) “Standard: Training. A covered entity must train all members of its workforce on the policies and procedures with respect to protected health information required by this subpart and subpart D of this part, as necessary and appropriate for the members of the workforce to carry out their functions within the covered entity.” Healthcare organizations, using ClearDATA Automated Safeguards or not, should also be documenting in their policies and procedures how to safeguard patient information as required by HIPAA 45 CFR §164.530(i)(1). Specifically, “A covered entity must implement policies and procedures with respect to protected health information that are designed to comply with the standards, implementation specifications, or other requirements of this subpart.” ClearDATA’s list of controls and Automated Safeguards can be included in customers policies and procedures, reducing the need for long documents and lengthy, arduous training.
Wrap Up
ClearDATA’s Automated Safeguard Data Feed provides a feedback loop that informs users of Google Cloud Platform when they violate healthcare compliance requirements. The logging events that describe the remediation action that occurred should also be built into our customer organization’s policies and procedures. Those policies and procedures should also describe how and when their employees are trained on safeguarding patient information, which should include ClearDATA’s set of compliance controls, Automated Safeguards, and what actions need to be taken after a remediation event occurs.
If you’d like to learn more about the services ClearDATA provides, please visit our webpage.



