The key to avoiding this kind of devastating blow to your organization is to understand HIPAA regulations around protecting sensitive health information and PHI. A good first step to protecting your organization is with a security risk assessment (SRA). An SRA has always been a good idea, but now it is more than that – it is also a requirement from the Office of Civil Rights who protects personal health information via HIPAA, and it helps demonstrate that you have a culture of compliance and are not being neglectful with PHI. The ever-present threats to PHI are well-known to regulators, which is why SRAs have been a longtime HIPAA priority. Starting in 2019, SRAs became a mandate to participate in the Merit-based Incentive Payment System (MIPS). Specifically, SRAs are one of the core requirements within the Advancing Care Information performance category in MIPs, and institutions competing for incentive funds can lose up to 6% if they do not have an SRA on file. A medical practice can do everything right from a value-based care perspective, but if it cannot demonstrate that it has an SRA on file, it is not eligible for the incentive funds.
Understanding Your Security Gaps Can Help Better Protect PHI
As I travel the U.S. to speak with healthcare organizations, it has become clear that every organization, from a small one doctor practice to a large hospital system, will have some security gaps. No organization is ever perfect, and the OCR knows this. But they need to see you trying to be. The most important thing is to identify your gaps before an incident or legal declaration of a breach occurs, so you can begin remediating.
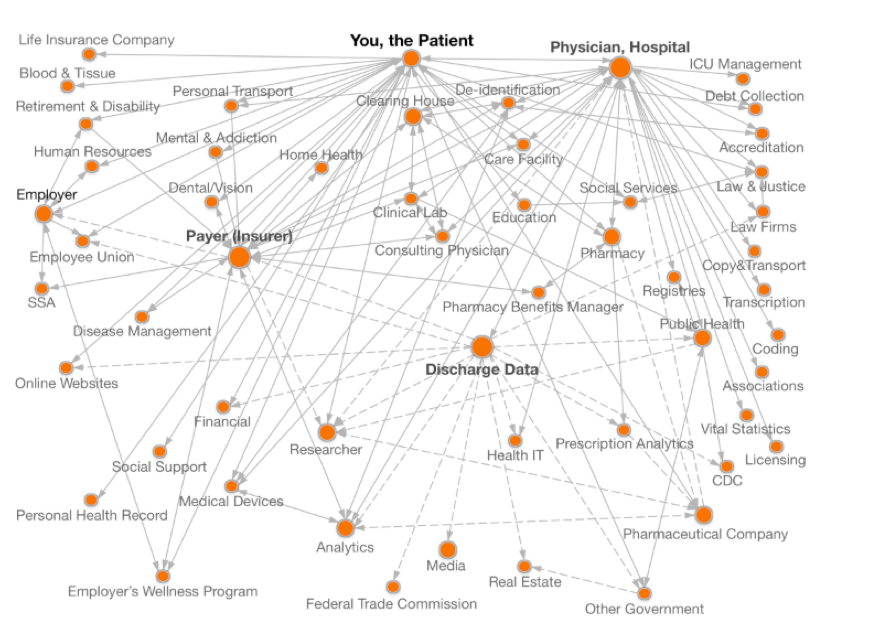
One of the primary reasons organizations struggle with understanding their security gaps is because they struggle to understand where their PHI actually is. This holds as true for a small clinic using on premise legacy infrastructure as it does for a larger organization in the public cloud. Because of data sprawl and shadow IT, as well as the sheer growing volume of healthcare data, it’s very difficult for most organizations to state with any certainty where ALL of their PHI is. And let’s face it, if you don’t know where it is, how can you protect it?
This image from theDataMap project[ii] at Harvard illustrates the problem. You can see how data sprawl can quickly become a crucial issue to address.
Three Common Security Gaps
I’m often asked what the most common security gaps are. There are three that come up again and again. Not surprisingly, the first is the lack of a PHI inventory. The second is related to encryption, and the third is around outdated or insufficient policies and procedures. Let’s dive deeper into each of those.
Lack of PHI Inventory
The best way to know where your PHI is, be it on premise, on the cloud, or across microservices, is to have a PHI Inventory. I recently spoke to a hospital system that expressed concerned that they had hundreds of workloads in the cloud and were no longer sure, with complete confidence, which had PHI.
Here’s the glitch. In the event of a security breach, the first thing (after calling your lawyer and reporting the breach) that is going to happen is the OCR is going to ask to see your security risk assessment and ask how many records were compromised. If you don’t know which PHI was compromised, you are forced to assume it was the highest possible number of records. Your fines can be as much as $1.5 million per incident, and there may have been several incidents in that one event. This does not include the enormous ongoing costs of remediation, credit protection for all of those whose privacy was compromised, and the loss in loyalty and reputation, all of which can combine to become a fatal blow to the organization. Additionally, behind that data is a human, and the cost to the patient or member can be devastating. As hackers increasingly target PHI theft, individuals who have been compromised are getting bills for procedures they never had. Someone may have had a hip replacement with your health insurance and the hospital may have paid $60K but now is sending you a bill for the remaining $20K. Another complication occurs when the person stealing the record changes the record and your care is compromised, sometimes creating potentially deadly scenarios. Imagine if they removed data stating that you are allergic to penicillin and you are admitted to a hospital with that detail not declared. Or, in the case I read about recently, a woman’s stolen health information was used to purchase opioids and to her surprise police showed up at her house and arrested her. Straightening out this kind of compromised or stolen record can take years and can delay the time it takes to give proper care to a patient in addition to wreaking havoc on the lives of those affected.
So, if PHI inventories are so important, why don’t all organizations have them? The challenges with conducting a thorough PHI inventory in-house are substantial. It is highly unlikely your IT team isn’t already working on business objectives full-time. How can they stop, and for how long, to conduct the inventory? Third-parties are a good path to take for this important step in protecting your patients and your organization. A third-party with expertise in conducting security risk assessments should make creating a PHI inventory a key initial step in their assessment.
Lack of Encryption
The second of the top three common security gaps is lack of encryption. I see massive problems with encryption across the healthcare space.
In our work, we find data at rest is not encrypted about 40% of the time and this creates a very attractive target to hackers.
Do you know if your data is properly encrypted? Not long ago, a large provider failed to encrypt data at rest and had approximately 80 million patient records stolen. Class action suits started; the fines began mounting. They had to hire a team of people just to send out all of the notification letters. When the OCR settled the case, in addition to the fines, the first matter of remediation they required was for that organization to get a third-party security risk assessment and risk remediation roadmap.
For smaller practices I speak with, especially the community hospitals operating with 3% or less margin, the cost for encryption software might seem unaffordable at anywhere from $3,000 – $5,000 –but consider the alternative with the cost of a breach. I worked with a small ophthalmology group not long ago that never thought they would be the victim of ransomware, but a hacker was able to get in and lock down their data. The CIO called me and said he was being charged $1,000 to get the data restored. If the hacker had understood HIPAA and realized he was holding PHI, he would have asked for $100,000, and it would still be cheaper to pay the ransom. Organizations have to protect themselves and their PHI better.
Lack of Current/Appropriate Policies and Procedures
The third most consistent security gap I see is around policies, with the number one offender being onboarding and offboarding employees. With incoming employees, it’s important to establish your culture of compliance from day one. Be sure they have adequate and ongoing training, and that the appropriate policies to safeguard your data are clear, especially as it relates to mobile devices which have been at the center of so many data breach news stories. With departing employees, the risk is even greater and rises if that employee is leaving disgruntled or against their will. Many may leave with short notice, or upon giving notice be excused because of the sensitive nature of the work they are exposed to. I see many companies that have neglected to check beyond the badge and laptop return to see if the employee has access to any PHI on any mobile device. Are there keys or passwords that should be shut off before they leave the building? Be thorough in how you onboard and offboard employees.
Request a Security Risk Assessment
Considerations When Preparing for Your Security Risk Assessment
Now that you understand the value of finding your security gaps before an incident or audit occurs, it’s time to decide if you want to conduct your SRA in house or outsource to a third party. Remember, a well-executed SRA not only plays a key role in finding your security and compliance gaps, it also forms the backbone of a remediation roadmap to get and keep you compliant.
And, with recent changes to MACRA and MIPS, it’s the vehicle that may help you earn up to 6% in incentive funding.
Buy vs. Build
You can conduct your own security risk assessment. Many of my SRA customers tried prior to contacting me. There are resources, including the OCR, that offer templates and spreadsheets for use in assessing your organization. I receive calls weekly from providers saying, “I downloaded this spreadsheet (or bought some software), and find myself saying yes more times than I suspect is accurate.” The real issue DIYers are facing is they don’t understand the context behind the question. And given HIPAA’s somewhat obscure “reasonable accommodation” standard, it takes someone with deep healthcare expertise to know if what you are doing is ‘reasonable.’ Another drawback I hear frequently from folks conducting their own SRA is it creates uncomfortable political situations within the organization. Imagine you are the head of IT and you uncover that your CIO is not properly encrypting data. Are you going to tell the CEO that your boss is exposing the company to hackers, and still feel comfortable about working there? But as much as the politics and lack of direct healthcare expertise can be problematic, there’s also the simple fact that I’ve never seen a healthcare IT organization that wasn’t already spread pretty thin. How will your IT team find the bandwidth to conduct the SRA? And the final consideration is keeping in mind that whoever files the SRA is the person who will be speaking with the OCR if there is a breach. Most of the people I speak with much prefer that to be a third party than someone on their team.
Understanding Safeguards
Let’s take a deeper look at the safeguards the OCR wants to know you have addressed in your SRA. When the OCR reviews your SRA they want to see that you are addressing safeguards under three key pillars.[iii]
Physical Safeguards
This group of safeguards looks at the actual physical environment in which the PHI is kept, transmitted or otherwise stored. Are laptops and server rooms locked? If you go to the OCR’s webpage where breaches are publicly displayed (also called the Wall of Shame throughout the industry, and someplace you don’t want to see your brand) you’ll see many instances where PHI was compromised by a stolen laptop or mobile device. If you don’t already do so, please enable remote wiping of your laptops in the event one is stolen.
I recently ran across a couple of good examples of what not to do with regard to physical safeguards. I was at a hospital last summer that had its own data center. I got there and it was hot and humid. The door to the data center was wide open. The servers were all exposed to dust, pollen, heat and humidity. But more than that, they weren’t secured physically. The team there said the HVAC was so dated and bad that when they closed the doors, the alarms went off because of the heat. There were probably 80,000 patient records and the doors were wide open.
In another instance, I was consulting at a clinic that had a drug distribution center in the back to help heroin or meth addicts come off the drugs. There was a back door the out-patients would come to for added privacy from what they could have in the front office. That office had a split door with the top open and the bottom locked. In the room was a table with a laptop with all patient records and a refrigerator with their treatment medications. The person staffing the clinic would sign the person in, then turn around and walk across the room to the refrigerator. That laptop was not tethered, and anyone could have reached in and stolen it. All of that PHI could have ended up in a pawn shop. Bottom line, physical safeguards are some of the easiest to comply with, yet people overlook them.
Technical Safeguards
A lot of focus is given to this set of safeguards, yet I still see a lack of proper encryption. The other big problem I’m seeing is people going DIY in the public cloud and not keeping up with data sprawl. Suddenly they have hundreds of workloads and no idea which have PHI. Another gap I see with technical safeguards is tech leaders with strong IT departments assuming all is well. You may have a great IT department, but the public clouds put out hundreds of new features a month. Unless you’re partnered with a third-party who is paying attention to each of those features, it’s hard to keep up. Additionally, most of the IT crews I meet do not include cloud-certified solution architects. My customers are often surprised by how many gaps they have in the technical safeguards.
Administrative Safeguards
This area is all about having solid, up-to-date policies and procedures, and consistently acting upon them. Do you have a clearly stated, enforced policy about onboarding and offboarding employees? What is your policy about shadow IT on personal mobile devices that are also being used for work? A significant issue I see here, prevalent across the Healthcare IT sector, is in the use of offshore vendors and independent contractors on 1099 forms. They aren’t given the same protocols as full-time employees and sometimes there is not even a Business Associate Agreement in place. These contractors are creating code and may have access to PHI without the proper security and compliance constraints in place.
The Power of Healthcare Exclusive, Cloud Expertise with HITRUST Certification
In closing, there are many advantages to setting yourself on solid ground by getting an external SRA. Many healthcare organizations turn to ClearDATA for this. ClearDATA is HITRUST certified, with extensive expertise in healthcare, privacy, security, and compliance on the cloud. Our ClearDATA Assess® software helps you identify your security gaps before a hacker does and helps covered entities and Business Associates meet the annual SRA requirement from HIPAA. Our team of experts guides you through the SRA process. Assess provides you with a portal where your team can collaborate to close security and compliance gaps, manage stakeholders and track progress with an audit trail.
Request an SRA
Whether you choose ClearDATA or opt to try this yourselves, feel free to use the following as a checklist for what you’ll need:
SRA Essential Components
- Review of PHI inventory to determine where electronic and other data is located
- Examination of the three safeguards required by 45 CFR 164.308 (a)(1) — administrative, physical and technical, including the latest Omnibus rules. (This is a facet many assessment providers overlook.)
- Assessment of current HIPAA security compliance operations, including safeguards in place, vulnerabilities, and specific threats to safeguards
- Evaluation of existing security policies and procedures
Recommendations and Remediation Road Map
- You should require a comprehensive, audit-ready report with findings and recommendations that includes detailed vulnerabilities and a remediation roadmap to help you prioritize what to fix first. Remediation may include outsourcing disaster recovery, backup and restore processes, information hosting, and perimeter testing through a HIPAA compliant, cloud-based infrastructure. With this option, both IT and security burdens are offloaded to seasoned experts.
HITRUST Certification
- Be sure whoever provides your SRA is HITRUST Certified against the Common Security Framework (CSF) from the Health Information Trust Alliance (HITRUST) to address HIPAA compliance requirements. Encompasses PCI, ISO 27001/2, NIST, COBIT, CMS and others.
Healthcare-Exclusive
- Because healthcare is so specifically regulated, I highly recommend finding an external SRA assessor who focuses on this industry. Someone focused solely on IT or cloud will not fully grasp the nuances that could be critical to you in understanding and addressing your security gaps.
SRA Implementation Expertise
- Proper and thorough implementation of your security risk assessment is absolutely essential to protecting your patients’ privacy, your company data, and in ensuring compliance with federal regulations.
While an external SRA is a good start, security and compliance should be stitched into everything you do. ClearDATA helps hundreds of healthcare and life sciences organizations stay compliant and secure as they develop and scale in the public clouds with our platform, solutions, and services. Our flagship solution ClearDATA Comply™ leverages automation and remediation and offers a Compliance Dashboard that provides you with a clear and concise view of your compliance posture at all times. Additionally, you will have visible mapping of technical controls to HIPAA regulations based on our extensive healthcare expertise. Contact us to learn more about how our solutions and services help you scale securely in the cloud.
Find Your Security Gaps Before a Hacker Does
____________________
[i] HIPAA Journal. Dec 28, 2017. https://www.hipaajournal.com/considered-phi-hipaa/
[i] HHS.gov Press Office. Oct 15, 2018. https://www.hhs.gov/about/news/2018/10/15/anthem-pays-ocr-16-million-record-hipaa-settlement-following-largest-health-data-breach-history.html
[ii] The Data Map, Harvard. https://thedatamap.org/map2013/index.php
[iii] U.S. Department of Health and Human Services, Office of Civil Rights. Security Risk Assessment Tool User Guide. https://www.healthit.gov/sites/default/files/page/2018-10/SRA_Tool_User_Guide_101518.pdf