There is no part of a compliance audit that won’t make you squirm like a toddler getting a haircut.
From the forced smiles of the initial meeting, the co-worker running his finger around the inside of his collar during the employee review, the seemingly-unrelenting scrutinization of your operational or financial paperwork during the department review, and finally the jury-delivering-its-verdict moment as you receive the final report.
At this juncture, let’s imagine that the audit is happening to someone else, creating a cautionary tale that your healthcare organization can learn from. What are some common gaps that are uncovered during a compliance audit? And what is IT’s role in resolving them?
The Healthcare Segments That Get Audited the Most
Carl Kunkleman, Senior Vice President and Co-Founder of ClearDATA, said the healthcare industry suffered more than 360 reportable breaches just last year, citing the U.S. Department of Health & Human Services’ website as his source, and not surprisingly, audits are on the rise. From over 20 years of experience on the frontline of sales, he sees providers getting audited the most out of any healthcare segment, but cautions that while providers may be audited the most frequently, breaches coupled with millions of dollars in fines are happening across all sectors in healthcare.
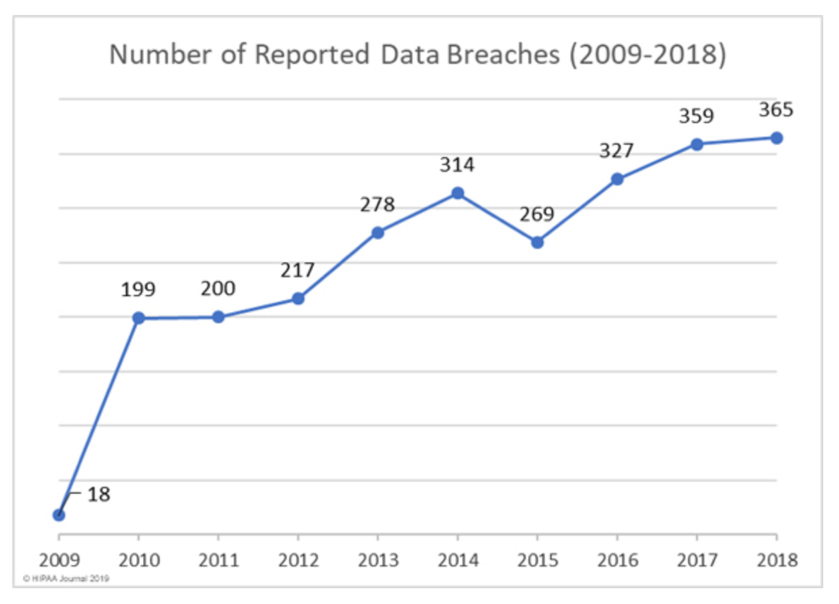
Source: HIPAA Journal 2019
The Most Common Gaps Uncovered During a Compliance Audit
- Lack of PHI inventory. On this, Kunkleman was very vehement, “I have never come to one hospital, one payer, one provider, one pharma, one life sciences company that has a thorough PHI inventory. It’s a universal problem in healthcare. If you don’t know where PHI lives, how do you know you’re protecting it?”
- Lack of encryption. Over thousands of visits to organizations across the healthcare industry, Kunkleman has discovered that data at rest is not encrypted about 40% of the time. He often sees lack of encryption in smaller providers. “Smaller practices are more hesitant about paying for encryption software. But consider the cost of each patient record lost and the thousands of dollars for an attorney to adjudicate yourOCR-level reportable breach.”
- Lack of current/appropriate Policies and Procedures (P&P). It’s important to establish a culture of compliance through ongoing security awareness training, appropriate policies regarding onboarding and offboarding employees, and smart protocols about who gets access to what and how much. You’d be surprised how often it’s simple things, like always keeping a server room door shut that get overlooked.
IT’s Role in Preventing Gaps and Helping to Avert a Crisis
Avoiding these gaps can be easier than resolving them, so IT departments should never assume an all-is-well mindset. The rate of innovation in the public clouds is mind-blowing—hundreds of updates a month which you have to be aware of if you don’t use a cloud services partner. Here are some of the most impactful preventative steps IT teams should be taking:
SRAs: the MRIs of PHI
One step IT teams can take is to set up a third-party security risk assessment (SRA) before you’re ever audited. After an audit, the Office of Civil Rights typically requires an organization to complete an SRA and update their risk remediation plan , so doing one when skies are calm is the best proactive security step an IT department can take. This also applies to conducting a thorough PHI inventory, and since IT’s time-constraints make doing this in-house burdensome, consider a third-party with expertise in conducting SRAs. It’s a smart twofer: a full PHI inventory and a comprehensive assessment of the security of your electronic health records—including encryption.
Breach simulation: optimize the effectiveness of your security controls
Kunkleman sees the irony in the data security status quo of some healthcare verticals,
“Hospitals may have great response policies as it relates to a hurricane or tornado. But what if you have a cyber–attack? It’s surprising how many don’t have a crisis communications plan in place for that!”
That’s where a breach simulation comes in. Conducted by a managed service provider that has both deep experience and understanding of the healthcare market, a breach simulation can help organizations discover and resolve their vulnerabilities. It’s like a fire drill where no one leaves the building—a tabletop simulation can generate a whole risk road map. The simulation can also bring something else to the light of day: which IT staffers aren’t suited for the pressure of a breach and which are. In an actual event, conference rooms can become panic rooms and finger pointing is not uncommon. It’s important to know in advance who can lead under pressure.
The chief compliance official: it pays to obey
By mandate, the healthcare industry is required to have a compliance official at every entity—whether it’s a doctor’s office or a big hospital system. It’s a difficult role because compliance officials have no direct control over IT, but they do have to train them. Today, you often see the Chief Compliance Officer’s (CCO) responsibilities being rolled under the CIO, because organizations know that’s where their data lives—and that pushes IT to give compliance more emphasis. And emphasis is truly needed to battle compliance fatigue as staff become tired of the same message and processes. CCOs must hatch up fresh ways to deliver and oversee compliance. Rapidly changing technology and regulation also presents new challenges, as falling behind often means the progression of potential risks. Is your organization’s CCO aware of the latest methods to track PHI inventories or optimize encryption? Here, an experienced, healthcare-focused MSP—that has compliance, privacy, and security as its main field of concentration—can make a big difference with staying current and fostering a culture of compliance.
Administrative safeguards for Policies and Procedures (P&P)
Beyond the technological aspects of an audit, organizations will be scrutinized for a lack of current or appropriate P&P. A defined policy regarding onboarding and offboarding personnel is key, with special attention given to the departing employees—particularly ones that have been fired. That can go beyond badge, keycard and laptop return. A shadow IT policy is also essential. Many workers employ their personal mobile devices to improve their productivity, but these devices are by far more vulnerable to the malicious activities of hackers and cybercriminals. And, the policies involving the contractors to your organization should address many of the same protocols as full-time employees, especially if outside contractors have access to PHI. So, while we are talking about policies and procedures that might sound administrative, IT teams can add significant value by eliminating security gaps.
It can be very challenging for healthcare organizations to test, analyze and remediate their own compliance gaps without interrupting day-to-day business operations. Yet, failure to do so can leave vulnerabilities unaddressed and put your business face-to-face with the data breach horror show.
It doesn’t have to be this way. IT can get support in preventing gaps or ensuring previous missteps don’t happen again. With ClearDATA—the healthcare-exclusive HITRUST-certified cloud solutions provider—you can have a partner that genuinely understands HIPAA and how vital it is to address compliance, privacy, and security—before you have an emergency.