Author: Conor Colgan
Solutions Architect
ClearDATA
Cloud Computing offers many benefits for healthcare organizations, from cost savings to hyper-scaling of services. And while engineers and developers often get excited about the newest services that allow for rapid adoption of new technologies, and IT leadership gets excited about the improved efficiency and potential for growth, IT Security & Compliance teams don’t tend to get excited about the prospect of putting Protected Health Information (PHI) and other sensitive data in the public cloud. It can be difficult to understand the requirements for properly securing and transmitting critical data, and the risks are high, which leads to slow adoption of certain technologies.
One of those technologies is known as the AWS Relational Database Service, or RDS. RDS makes it easy to set up, operate, and scale various relational database engines such as MySQL and Microsoft SQL. RDS contains a number of built-in features, such as automated patching and backups that remove a large operational burden from database administrators and allow them to focus on optimization rather than time consuming maintenance activities. In my experience with database administrators, some of their most time consuming tasks are the configuration of a highly available database (ask any DBA about configuring and monitoring log shipping) and software patching. RDS handles the burden of both of those tasks, allowing the database administrator to focus on the data and the database.
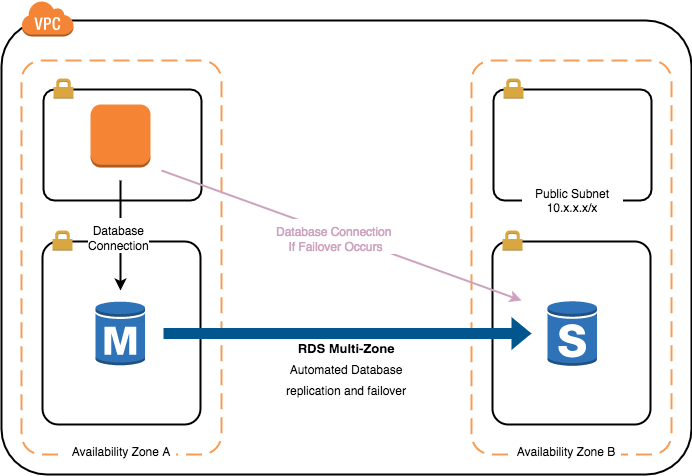
ClearDATA™ builds and deploys using repeatable processes that deploy RDS instances with security and compliance as a primary foundation. For example, one of the primary requirements for storing PHI in any system is that the data must be encrypted at rest. ClearDATA utilizes AWS KMS keys to ensure data stored at rest in the underlying storage system are encrypted. ClearDATA also encrypts in motion by enforcing encrypted connections to the database itself, where available. The encrypted connections are built into the deployment template, and then interrogated and audited by the ClearDATA Compliance Dashboard.
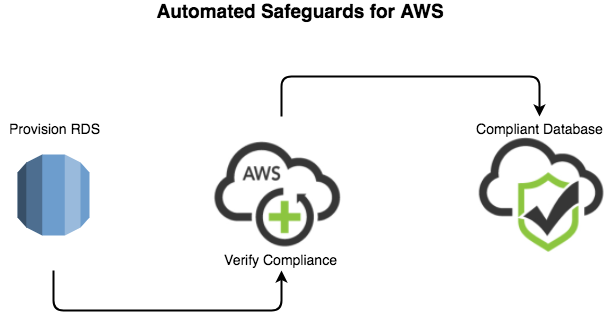
At this point, you might think, “what happens if a database is deployed without a template?” Experienced AWS users often programmatically create databases, and those may not utilize a full CloudFormation template. ClearDATA closes that gap with our Automated Safeguards for AWS. ClearDATA employs a powerful set of tools in customer accounts that monitor for state changes, and if the newly created database instance does not meet the compliance standards, the instance can be suspended or terminated to minimize the risk associated with a non-compliant database. This ensures that no matter who or how the database instance is created, data is not put at risk.
The ClearDATA Compliance Dashboard provides visibility into the database service, ensuring that the automation and templated deployment of the database adheres to the compliance requirements. This allows everyone from engineers to the Chief Privacy Officer to ensure the database storing critical and protected information is running in a compliant manner. It’s not just a matter of ensuring that the initial deployment was done in a compliant manner, but also that the ongoing operations of the database maintain that culture of compliance. This includes things like automated backups to comply with HIPAA Technical Safeguard 45 CFR §164.308(a)(7)(ii)(B), audit logging to comply with HIPAA Technical Safeguard 45 CFR § 164.312(b), and built-in high availability to comply with HIPAA Technical Safeguard 45 CFR §164.310(a)(2)(i).
The automatic deployment of these features helps healthcare and life sciences customers quickly deploy databases in the public cloud capable of safely hosting PHI and PII. Engineers and developers can take advantage of some of the great features of RDS (read replicas, cross-region replication, etc.); IT Leadership sees the advantages of a focused database administration team, as well as the scaling options available to grow the business; and the IT Security & Compliance teams can sleep well knowing that PHI and PII data is protected and safe.


